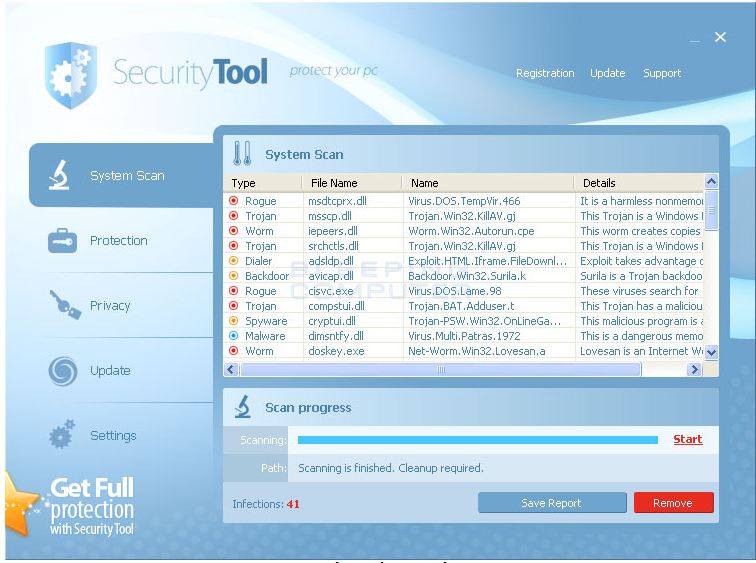
I found that running malwarebytes anti-malware was not enough, nor in safe mode either. even with hijackthis and killing off some autoloaders it did not work.
this is a service running in the system as it starts, so you can download the following fixes:
hostsperm.bat (JUST NORMALLY NOT IN SAFE MODE)
this allows the operating system to regain editing ability of the HOSTS file by everyone
allows you to clear the infected hosts file (remember if you had hosts setting you added to replace them after this)
open a text editor, put in this code and save to your desktop as hostsperm.bat (change .txt to *.* in notepad so you dont get hostsperm.bat.txt!)
Code: Select all
@echo off
echo,Y|cacls "%WinDir%\system32\drivers\etc\hosts" /G everyone:f
attrib -s -h -r "%WinDir%\system32\drivers\etc\hosts"there is no extension (.txt etc) so you can show hidden files if you use explorer to get to the folders, and then right click and OPEN
then choose, say, notepad.exe to open, edit, and save with
HOSTS files for various WIN OS systems
xp http://download.bleepingcomputer.com/mi ... s-xp/hosts
Code: Select all
# Copyright (c) 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
127.0.0.1 localhostserver 2003 http://download.bleepingcomputer.com/mi ... rver/hosts
server 2008 http://download.bleepingcomputer.com/mi ... rver/hosts
7 http://download.bleepingcomputer.com/mi ... ws-7/hosts
rkill (JUST NORMALLY NOT IN SAFE MODE)
http://download.bleepingcomputer.com/grinler/rkill.exe
*you must copy and paste rkill from the web, or from a usb key from a good computer to yours and say put it on your desktop
then restart your pc and as soon as your desktop shows up, run rkill by left cliking and pressing enter for instance
*if you find that your desktop is missing, you can run malwarebytes antimalware in safe mode and clean up 'most' of the problem so in normal mode you see your desktop or
obviously if you opt to just do this and then run rkill really quickly before the 'security tool' services run, you'd better be fast. really fast.Click on the Start button and type %UserProfile%\desktop in the Search field at the bottom of the start menu. Then press Enter on your keyboard.
Malwarebytes anti-malware (JUST NORMALLY NOT IN SAFE MODE)
http://download.cnet.com/Malwarebytes-A ... 04572.html
after rkill, run malwarebytes antimalware (JUST NORMALLY NOT IN SAFE MODE)
a. quick or full scan
b. show results when done
c. remove threats
d. restart normally [yes]